SHIELD
To enable higher resiliency, improved efficiency, and new capabilities
Dynamic, multifunction service that enables high volume, high call control with small footprint. Delivers revenue growth, margin, capex and opex savings opportunities.
25%
Fraud Loss Reduction
30%
Network Cost Savings
25M+
Calls Per Day
What is Shield?
Dynamic Multifunction Service
Enables high volume, high call control with small footprint. Cost effective and highly flexible with multiple deployment options including as a service option.
Revenue Growth & Savings
Delivers revenue growth, margin, capex and opex savings opportunities. Creates port savings reducing capex and support fees.
Easy Integration
Easy to enable, complimentary to existing OSS/BSS and products. Custom variables and custom products are easily configured and deployed.
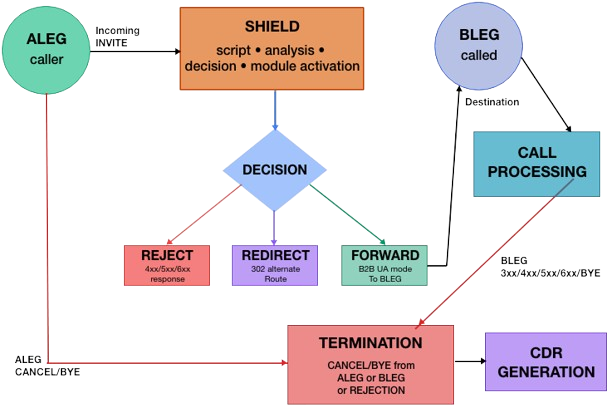
Intelligent Real-Time Call Control
SHIELD processes every call through a sophisticated decision engine that analyzes, filters, and routes traffic in real-time. Our advanced script engine evaluates each call against configurable rules, activating the appropriate modules to optimize your network performance.
- Call Reception (ALEG)
SHIELD receives incoming SIP INVITE messages from callers
Every call is immediately captured for analysis
Sub-100ms processing ensures no impact on call quality - Script Engine Analysis
Advanced algorithms evaluate call characteristics
Multiple detection modules activate based on call attributes
Configurable rules engine processes calls against your criteria
Real-time decision making with comprehensive call intelligence
- Three-Path Decision Process
REJECT Path - Block unwanted traffic
Returns 4xx, 5xx, or 6xx SIP responses
Prevents fraudulent, spam, or low-quality calls
Immediate cost savings by blocking bad traffic
Protects network resources and capacity
REDIRECT Path - Intelligent call routing
Issues 302 redirect responses with alternate destinations
Enables advanced load balancing and traffic management
Optimizes routing based on real-time network conditions
Maintains call flow while directing to best endpoints
FORWARD Path - Process legitimate calls
Operates in Back-to-Back User Agent (B2BUA) mode
Forwards approved calls to destination (BLEG)
Maintains full visibility and control throughout call lifecycle
Enables advanced features like transcoding and recording
- Call Processing & Monitoring
Forwarded calls proceed through normal processing
SHIELD maintains visibility throughout the entire call
Real-time monitoring of call quality and performance
Continuous analysis for optimization opportunities
- Call Termination Handling
Handles termination from either calling party (ALEG) or destination (BLEG)
Processes CANCEL and BYE messages appropriately
Manages call rejection scenarios gracefully
Ensures proper cleanup and resource management - Comprehensive Call Detail Records
Generates detailed CDRs for all call attempts
Includes analysis results, routing decisions, and performance metrics
Integrates with billing systems and analytics platforms
Provides actionable insights for network optimization

Creative Solutions
Multiple solutions all running on the same code differentiated by scripting and components
Shield
Comprehensive Network Protection
- Fully aware SHIELD, all SBC ports utilized to manage load
- Rules Engine blocking – saves money
- Same Billing/Routing etc as today
- Increased customer resiliency
- Improved vendor utilization and efficiency
- Eliminates hot spots with load balancing
DIP including LNP
Real-Time Database Intelligence
- Local Number Portability (LNP) dipping
- STIR/SHAKEN certificate verification and stamping
- HLR and RNDB integration
- Call verification and enrichment
- 24-hour TTL caching for disaster recovery
- Multi-party LNP and CIC analysis
Peering
Controlled Interconnection Platform
- Toll-free and DID traffic management
- USA/Canada/Extended NPA/Global support
- CPS and concurrent call controls
- Attestation level & S/S information screening
- Compensation level management
- Native codec transit support
Network Extension
Global Presence Solution
- In-country presence for multiple customers
- Local IP assignment by customer
- Shared or dedicated media options
- Multiple host configurations
- CDR streaming to existing infrastructure
- SIP signaling header customization
Risk
Advanced Threat Assessment
- Multi-party LNP and HLR analysis
- Private and service DNO screening
- CNAM and policy enforcement
- In-call flow analytics
- Sub-100ms routing decisions
- A, B, A/B number intelligence
Customized
Tailored Business Solutions
- Custom scripting and configurations
- Business-specific rule engines
- Flexible deployment options
- GUI tailored for operations
- Third-party integration support
- Variable rule sets and grey listing
KPIs
Take action on measured KPIs in real-time
- Choose from the following
Answer Seizure Ratio (ASR), Average Call Duration (ACD), Post Dial Delay (PDD), Stir/Shaken Verify, Average Setup Time (AST), Network Efficiency Ratio (NER), Call Cancel Ratio (CXR), Bye Ratio Direction (BYERD), Answer Time to Ring Variation (ATRV), One Way Audio Bye (OWAB), One Way Audio (OWA) - KPI Timing configuration and measurement frequency
- Further Call Enrichment
black or grey list the call with TTL
additional call enrichment based on port, lnp, spid, public and private data, stir/shaken information for A#, B# or A/B# - Take Action
call rejection, call route change, call treatment change
Shield and AI Integration
SHIELD's AI models process vast amounts of telecom data in real-time
to make intelligent routing decisions, detect fraud patterns, and optimize network performance.
Data Collection & Processing
Call Detail Records (CDRs): Call setup, duration, and termination data; Route selection and carrier performance; Quality metrics (ASR, ACD, PDD, etc..)
LNP Intelligence: Service Provider ID tracking (SPID); Number porting timeline analysis; Origin and destination carrier mapping; Carrier Type classification; Historical porting patterns and trends
Network KPIs & Behavioral Data:
STIR/SHAKEN certificate authenticity; Geographic risk profiling; Calling pattern anomalies; Fraud signatures and indicators; Network efficiency metrics
AI Models & Applications
Fraud Detection: Predictive Risk Scoring; 0-1000 dynamic risk assessment; Pattern recognition for wangiri, IRSF; Fresh port number flagging; Carrier reputation modeling
Intelligent Routing: Adaptive Path Selection; Real-time route optimization; Carrier performance prediction; Cost vs quality optimization; Load balancing algorithms
Behavioral Analytics: Call Pattern Intelligence; Calling frequency analysis; Geographic correlation modeling; Time-based pattern detection; Customer lifecycle attribution
Predictive Network Optimization: Proactive Performance Tuning; Capacity planning predictions; Quality degradation forecasting; Maintenance scheduling optimization; Resource allocation modeling
Real-Time Intelligence
Sub-100ms Decision Making: AI models process multiple data points instantaneously to make routing decisions without impacting call quality.
Continuous Learning: Models adapt and improve based on network feedback, fraud outcomes, and changing traffic patterns.
Multi-Source Data Fusion: Combines CDR data, LNP intelligence, KPI metrics, and external threat feeds for comprehensive analysis.
Proven Results.
- Network Utilization Improvement
Port reduction with 97% margin retainment30%
A# rule of ASR/ACD requirements (100 calls 10% ASR/12 ACD) - High Performance Processing
On 2 CPUs with CDR generation and increased resiliency325cps
Origin capacity and numbering filtering with portability termination dipping - Call Optimization
Call rejection while retaining 99% margin and revenue>10%
Within 24 hours of deployment, increasing LCR route utilization - IRSF Fraud Protection
Routing decisions in real timeSub-100ms
Reduce IRSF fraud exposure due to hack and wangiri by code defined capacity limits - Port Requirement Reduction
Reduction in port requirements~8%
Consistent rejection of calls for unallocated numbers - Production Scale
Calls per day processed in production25M+
Currently deployed across North America and Europe
Real-World Use Cases
Shield delivers measurable results across multiple scenarios

Fraud Preventiontransforming call centers with fraud detection and smart routing
Shield provides intelligent fraud detection to automatically block suspicious calls while fast-tracking legitimate customers through priority queues. The system analyzes caller patterns, geographic risk factors, and carrier reputation in real-time, assigning risk scores from 0-1000 to route calls appropriately. This prevents scammers from wasting valuable agent time while ensuring genuine customers receive faster, higher-quality service.
The Challenge
Overwhelming Volume: Call centers flooded with both legitimate and fraudulent callsResource Drain: Agents waste valuable time with potential scammers
Customer Experience: Genuine callers face longer wait times
Security Vulnerability: Traditional screening methods easily circumvented
Smart Call Scoring System
Porting: Fresh number ports flagged as potential risk indicatorsCarrier Reputation: Identifies calls from known problematic sources
STIR/SHAKEN Verification: Authenticates caller identity with industry standards
Behavior Patterns: Maps calling frequency and suspicious patterns
Geo Assessment: Evaluates calls from high-fraud-rate regions
LNP Dipping: Real-time ownership verification of calling numbers
Dynamic Risk Scoring Engine
Weighted Algorithms: Tailored to your specific business threat landscapeComprehensive 0-1000 Scale: Granular scoring for precise call categorization
Sub-100ms Processing: Lightning-fast decisions without call quality impact
Self-Learning: Improves accuracy through continuous feedback
Smart Queue Management
Premium Lane (0-300): VIP experience for verified legitimate callers - Priority routing, Reduced wait times, Top agent assignmentVerification Lane (301-700): Additional screening for medium-risk calls - Secondary verification measures, Standard queue placement, Monitored interactions
Honeypot Diversion (701-1000): Specialized handling for high-risk calls - Isolation from legitimate call flow, Advanced fraud confirmation protocols, Data collection for threat intelligence
Egress Filteringadvanced outbound call filtering for revenue protection
Shield's Call Egress Filtering prevents unauthorized outbound calls that cause quality issues, regulatory violations, and revenue loss. The system uses geographic intelligence, numbering plan analysis, and carrier profiling to validate calls in real-time before routing. Advanced decision matrix processing (sub-100ms) ensures compliance with regional restrictions while optimizing network capacity through configurable filtering rules and dynamic route selection.
The Challenge
Quality Control Issues: Unfiltered outbound calls leading to poor connection qualityRegulatory Compliance: Need to enforce region-specific calling restrictions
Revenue Protection: Preventing unauthorized routes that impact profitability
Resource Optimization: Efficient utilization of network capacity
Dynamic Egress Filtering
Geographic Intelligence: Country and area code-based routing decisionsNumbering Plan Analysis: Validates against authorized dialing patterns
MNP Integration: Real-time number portability verification
Carrier Profile Matching: Routes based on originating carrier attributes
Regulatory Compliance: Enforces legal restrictions by jurisdiction
Rate Protection: Guards premium destinations from inappropriate traffic
Advanced Decision Matrix
Real-Time Processing: ub-100ms filtering decisions without call quality impactHierarchical Rule Application: Cascading filter logic for precision control
Dynamic Route Selection: Adapts routing based on specific number attributes
Granular Call Rejection: Targeted blocking with appropriate reason codes
Pattern Recognition: Analyzes call characteristics against rule templates
Deep Packet Inspection: Examines signaling metadata for comprehensive decisions
Configurable Filtering Parameters
Allow list/Blocklist Management: Define permitted or restricted destinationsCategorized Country Groups: Organize destinations by region or risk profile
Prefix-Based Controls: Target specific ranges within country codes
Expression-Based Logic: Create complex rules with boolean operators
Time-Based Restrictions: Apply rules based on time of day/week
Carrier-Specific Policies: Different rules for different interconnect partners
Our Implementation Approach

Discovery
Assessment of current fraud patterns and egress routing analysis

Configuration
Algorithm customization, weight assignment, and rule definition

Integration
Seamless deployment with existing systems and controlled testing

Testing
Controlled rollout with performance monitoring and validation

Optimization
Continuous refinement based on real-world results and feedback
Why you should choose Shield..
Adaptive Security
Evolves with changing fraud tactics and threat landscape
Operational Efficiency
Maximizes agent productivity and network utilization
Customer Satisfaction
Prioritizes legitimate callers for optimal experience
ROI Focus
Reduces losses while improving performance and margins
Seamless Integration
Works with your existing infrastructure without disruption
Comprehensive Reporting
Full visibility into filtering decisions and outcomes